Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Last updated 20 setembro 2024

This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
portswigger/README.md at master · roberson-io/portswigger · GitHub

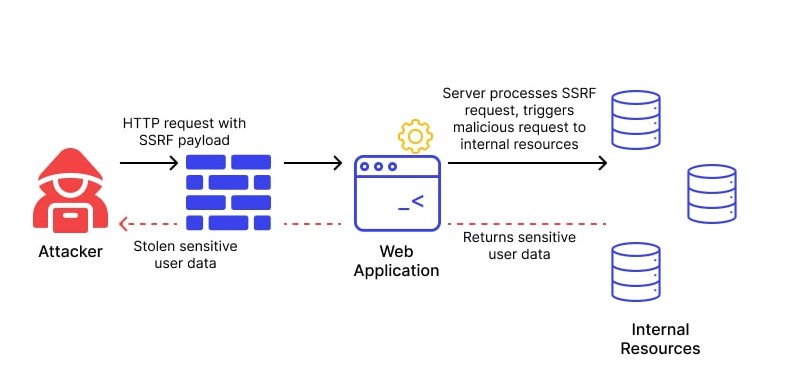
Free Cybersecurity & Hacking Training
SSRF (Server Side Request Forgery) - HackTricks - Boitatech

Linux Exploitation – Shellshock exploit and privilege escalation
Exploiting Blind SSRF - Passion

Exploiting XML-RPC on WordPress that is protected by NGINX : r

翻译]盲SSRF利用链术语表-腾讯云开发者社区-腾讯云

Penetration Testing Step 3 – Blind SSRF attack với hàng độc out-of

HackMD - Collaborative Markdown Knowledge Base
Server Side Request Forgery · master · pentest-tools
Website Hacking Archives - Hackercool Magazine
Recomendado para você
-
Buy ShellShock Live Steam Key RU/CIS - Cheap - !20 setembro 2024
-
Lab Walkthrough - Shockin' Shells: ShellShock (CVE-2014-6271)20 setembro 2024
-
 Shellshock Vulnerability and Attack20 setembro 2024
Shellshock Vulnerability and Attack20 setembro 2024 -
 Shellshock Exploit Hack | Sticker20 setembro 2024
Shellshock Exploit Hack | Sticker20 setembro 2024 -
 Yahoo confirms servers infected — but not by Shellshock20 setembro 2024
Yahoo confirms servers infected — but not by Shellshock20 setembro 2024 -
Shellshock: Bash software bug leaves up to 500 million computers at risk of hacking - ABC News20 setembro 2024
-
 Shellshock Bug May Be Even Bigger Than Heartbleed: What You Need to Know - ABC News20 setembro 2024
Shellshock Bug May Be Even Bigger Than Heartbleed: What You Need to Know - ABC News20 setembro 2024 -
 Shellshock proves open source's 'many eyes' can't see straight20 setembro 2024
Shellshock proves open source's 'many eyes' can't see straight20 setembro 2024 -
 BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek20 setembro 2024
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek20 setembro 2024 -
 Hacks - TMNT of Rage - The Final Shell Shock & Re-Shelled20 setembro 2024
Hacks - TMNT of Rage - The Final Shell Shock & Re-Shelled20 setembro 2024
você pode gostar
-
 NEW Roblox Action Collection TOWER DEFENSE SIMULATOR LAST STAND20 setembro 2024
NEW Roblox Action Collection TOWER DEFENSE SIMULATOR LAST STAND20 setembro 2024 -
A Fazenda 14 – Conheça o site oficial do reality show – Record TV20 setembro 2024
-
 Space Wars: Cantina - Simple set I scored off of Temu for $17 : r/lepin20 setembro 2024
Space Wars: Cantina - Simple set I scored off of Temu for $17 : r/lepin20 setembro 2024 -
 Pokemon Super Neo Metal Sonic20 setembro 2024
Pokemon Super Neo Metal Sonic20 setembro 2024 -
 Monkey D. Luffy Monkey d luffy, One piece luffy, Luffy20 setembro 2024
Monkey D. Luffy Monkey d luffy, One piece luffy, Luffy20 setembro 2024 -
Depois que inventaram o soca fofo “ os homens “ 🤣🤣🤣 #explore20 setembro 2024
-
 Pokemon Pokemon: White Version 2 Strategy Guides20 setembro 2024
Pokemon Pokemon: White Version 2 Strategy Guides20 setembro 2024 -
 Assistir Isekai Meikyuu de Harem wo (Sem Censura) - Todos os20 setembro 2024
Assistir Isekai Meikyuu de Harem wo (Sem Censura) - Todos os20 setembro 2024 -
 Gish' at 30: Revisiting The Smashing Pumpkins' spiritual debut album - Far Out Magazine20 setembro 2024
Gish' at 30: Revisiting The Smashing Pumpkins' spiritual debut album - Far Out Magazine20 setembro 2024 -
 Kit Alpaca Faca Chef 8 + Faca Churrasqueiro 9 Nó Espanhol +20 setembro 2024
Kit Alpaca Faca Chef 8 + Faca Churrasqueiro 9 Nó Espanhol +20 setembro 2024



