Malware analysis Malicious activity
Por um escritor misterioso
Last updated 22 setembro 2024

Malware Analysis: Steps & Examples - CrowdStrike

Nextron Systems - We Detect Hackers
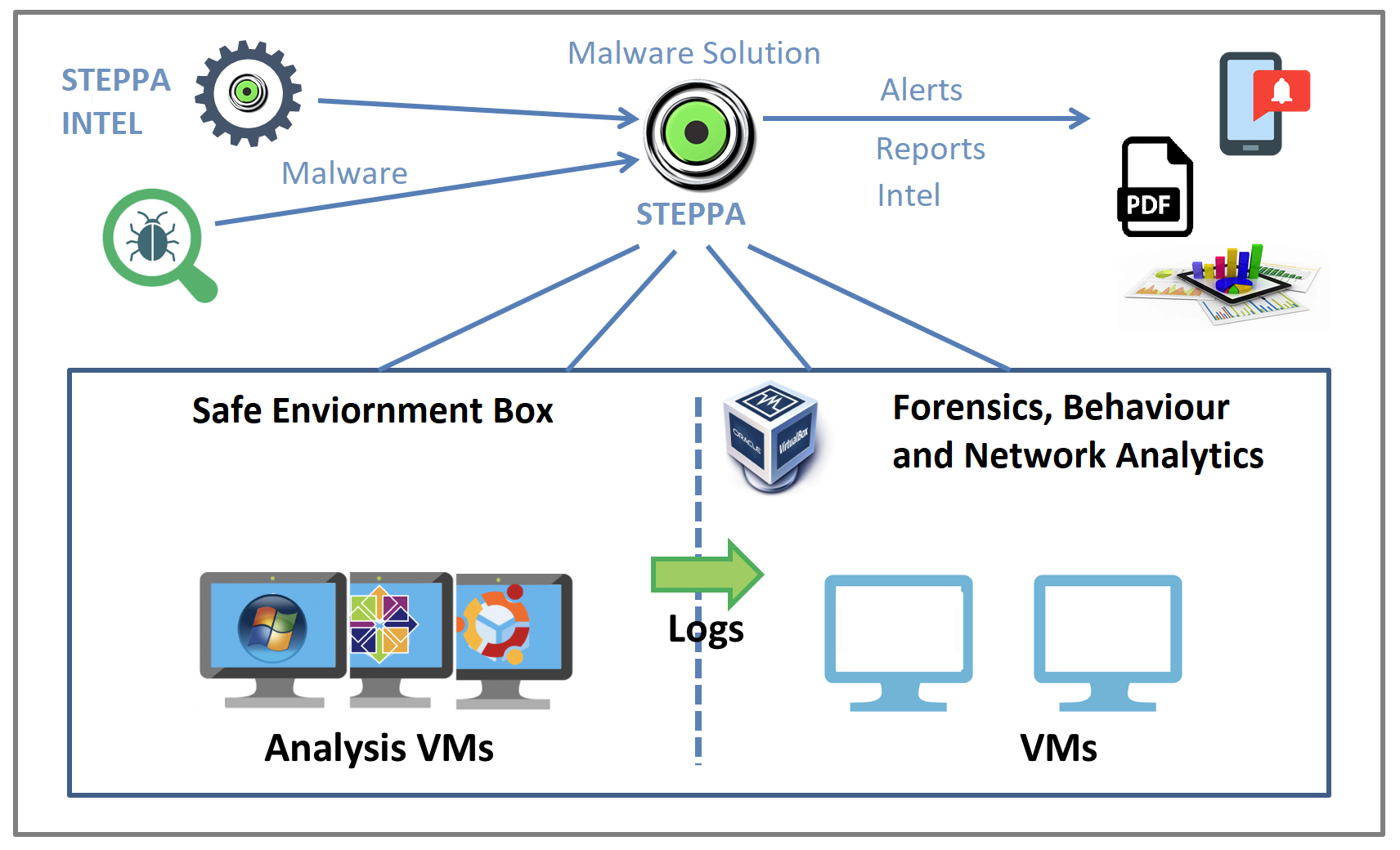
Malware Analysis Solution: Analyze, Detect, and Protect

Malware analysis mykey_.rar Malicious activity

Detail procedure of malware analysis
Malware analysis 1071d6d497a10cef44db396c07ccde65 Malicious activity

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
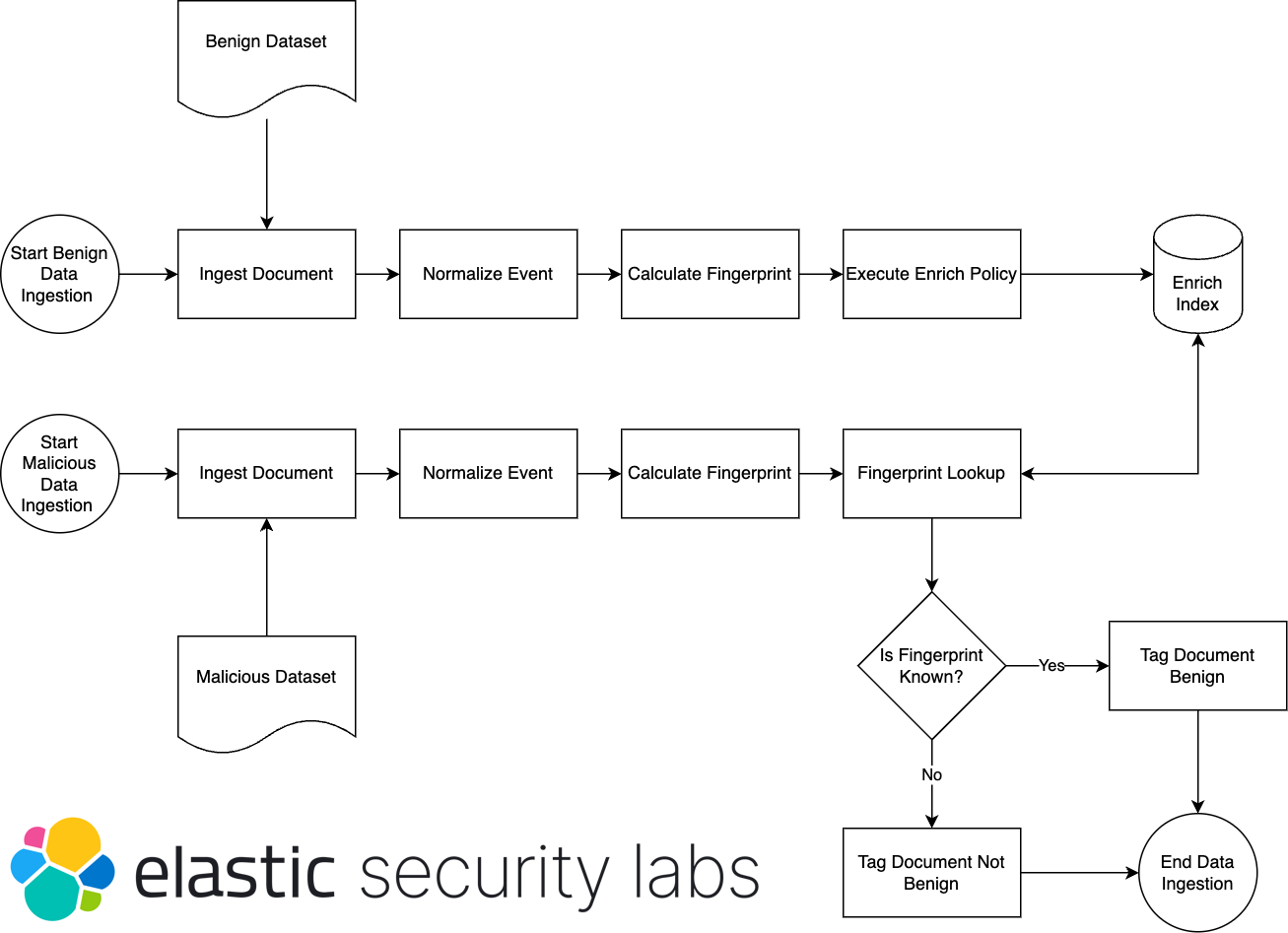
An Elastic approach to large-scale dynamic malware analysis — Elastic Security Labs

Cybersecurity Search Engine

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

What is Malware? Definition, Types, Prevention - TechTarget
MetaDefender Cloud Advanced threat prevention and detection

How to Analyze Malware's Network Traffic in A Sandbox
Recomendado para você
-
 Jjsploit V4-Www.Wearedevs.Net - Colaboratory22 setembro 2024
Jjsploit V4-Www.Wearedevs.Net - Colaboratory22 setembro 2024 -
 Wearedevs22 setembro 2024
Wearedevs22 setembro 2024 -
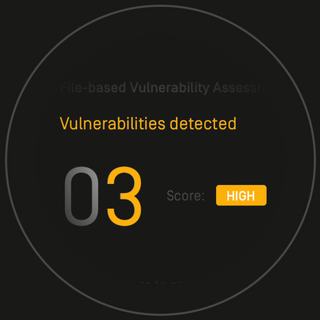
 Malware analysis Malicious activity22 setembro 2024
Malware analysis Malicious activity22 setembro 2024 -
WeAreDevs++ Beta22 setembro 2024
-
roblox-executor · GitHub Topics · GitHub22 setembro 2024
-
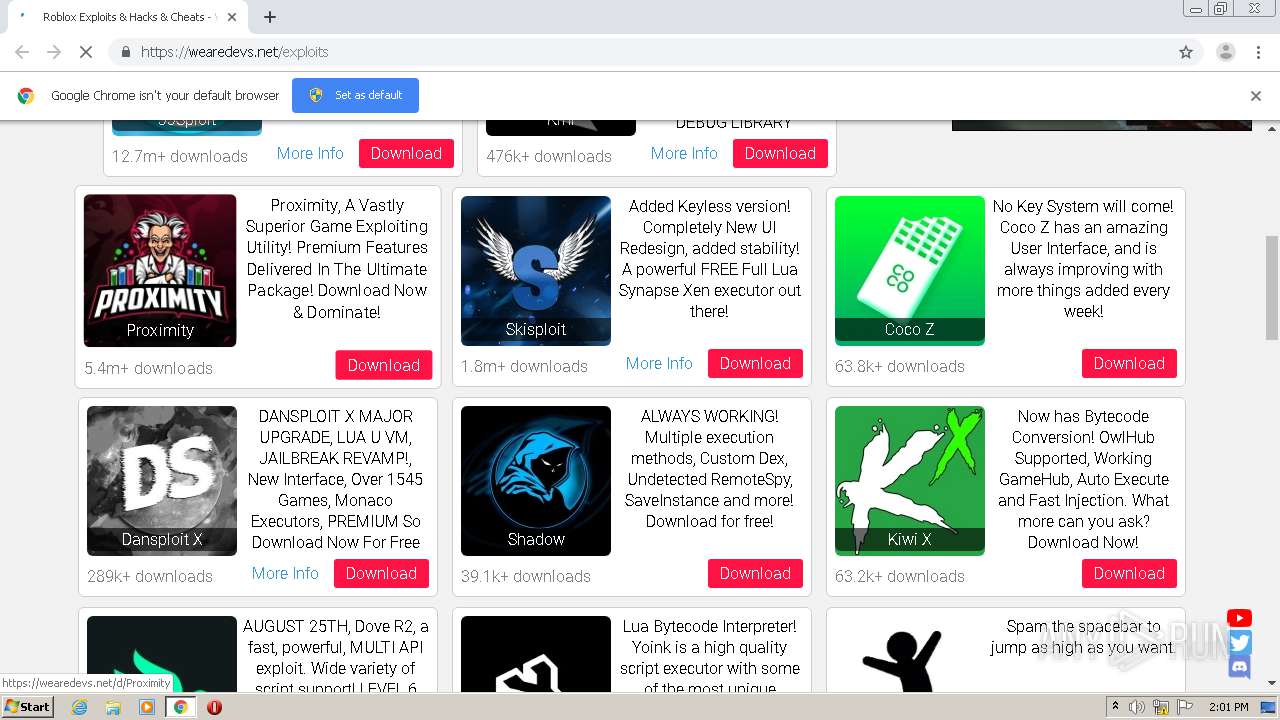
 Home - WeAreDevs22 setembro 2024
Home - WeAreDevs22 setembro 2024 -
roblox-scripts · GitHub Topics · GitHub22 setembro 2024
-
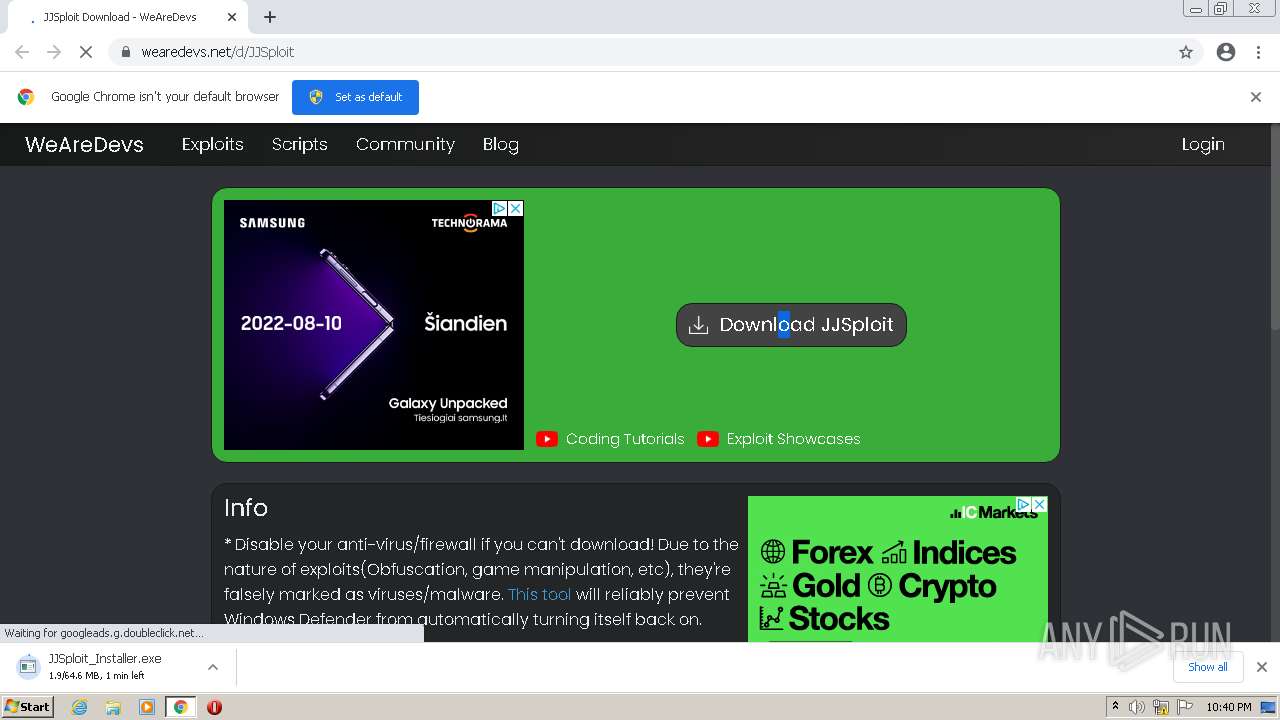 Malware analysis Malicious activity22 setembro 2024
Malware analysis Malicious activity22 setembro 2024 -
 Why cant i use krnl : r/Krnl22 setembro 2024
Why cant i use krnl : r/Krnl22 setembro 2024 -
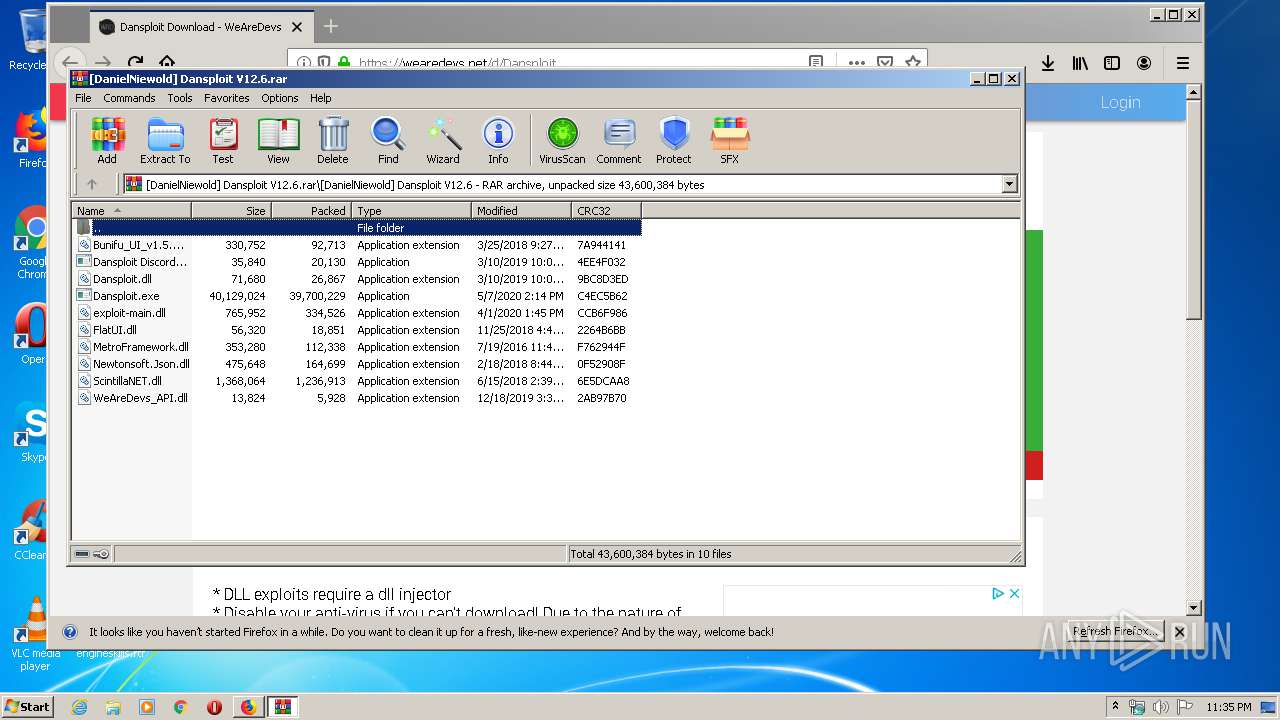 Malware analysis Malicious activity22 setembro 2024
Malware analysis Malicious activity22 setembro 2024
você pode gostar
-
 Zoo Tycoon Ultimate Animal Collection PC Steam Digital Global (No Key)22 setembro 2024
Zoo Tycoon Ultimate Animal Collection PC Steam Digital Global (No Key)22 setembro 2024 -
 super mario – Dr. K's Waiting Room22 setembro 2024
super mario – Dr. K's Waiting Room22 setembro 2024 -
 M Gengar-EX (Phantom Forces 35) - Bulbapedia, the community-driven22 setembro 2024
M Gengar-EX (Phantom Forces 35) - Bulbapedia, the community-driven22 setembro 2024 -
 SYX MOTO Blitz Gas Powered Kids Dirt Bike, 50cc 2 Stroke, Pull22 setembro 2024
SYX MOTO Blitz Gas Powered Kids Dirt Bike, 50cc 2 Stroke, Pull22 setembro 2024 -
 Video Game 'Bloodborne' Forges Connections During Quarantine : NPR22 setembro 2024
Video Game 'Bloodborne' Forges Connections During Quarantine : NPR22 setembro 2024 -
1 Chapter 418 - Komi-san wa Komyushou Desu. - MangaDex22 setembro 2024
-
 Feedback on a GFX - Creations Feedback - Developer Forum22 setembro 2024
Feedback on a GFX - Creations Feedback - Developer Forum22 setembro 2024 -
 Viajando de volta para os anos 2000: explorando o Windows 98 e alguns jogos com EmuPedia22 setembro 2024
Viajando de volta para os anos 2000: explorando o Windows 98 e alguns jogos com EmuPedia22 setembro 2024 -
 Digibyte Digibyte Giveaway GIF - Digibyte Digibyte Giveaway22 setembro 2024
Digibyte Digibyte Giveaway GIF - Digibyte Digibyte Giveaway22 setembro 2024 -
 Daigo Shigeno/Image Gallery, Major Wiki, Fandom22 setembro 2024
Daigo Shigeno/Image Gallery, Major Wiki, Fandom22 setembro 2024