Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 20 setembro 2024

Describing activities of a crime group attacking Ukraine.

System model of attribute-based access control for proxy re-encryption

Vault 7 - Wikipedia

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

Target and solution of DoS attacks (source: authors' work)

Initial Access Brokers Fueling Ransomware

US20080120240A1 - Trusted infrastructure support systems, methods and techniques for secure electronic commerce, electronic transactions, commerce process control and automation, distributed computing, and rights management - Google Patents
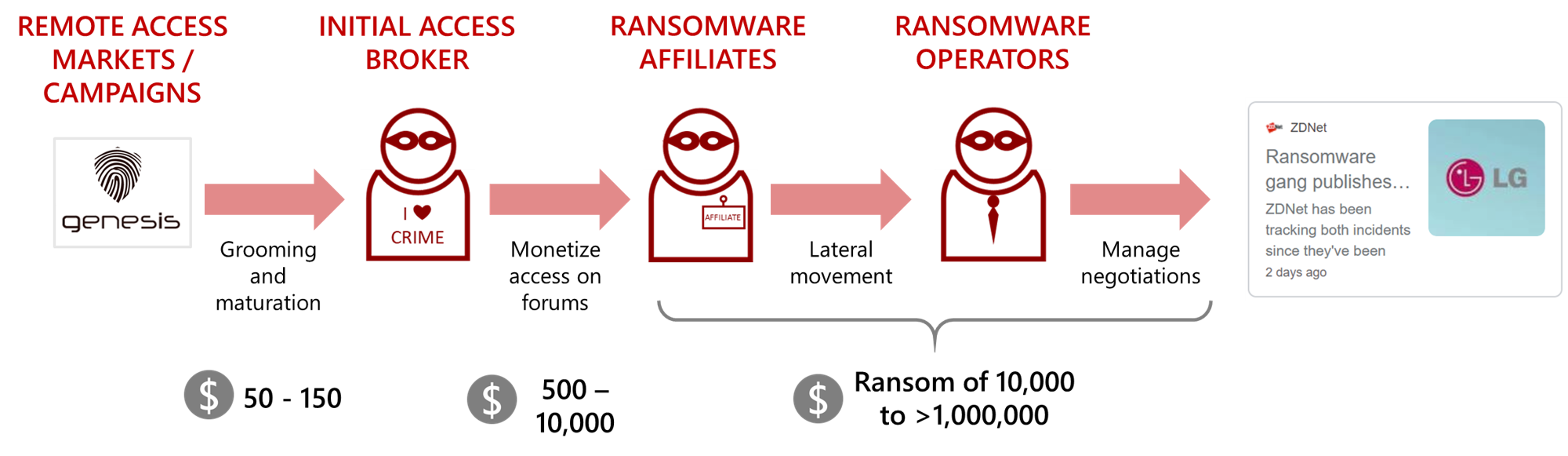
The Secret Life of an Initial Access Broker • KELA Cyber Threat Intelligence
Cybersecurity Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore
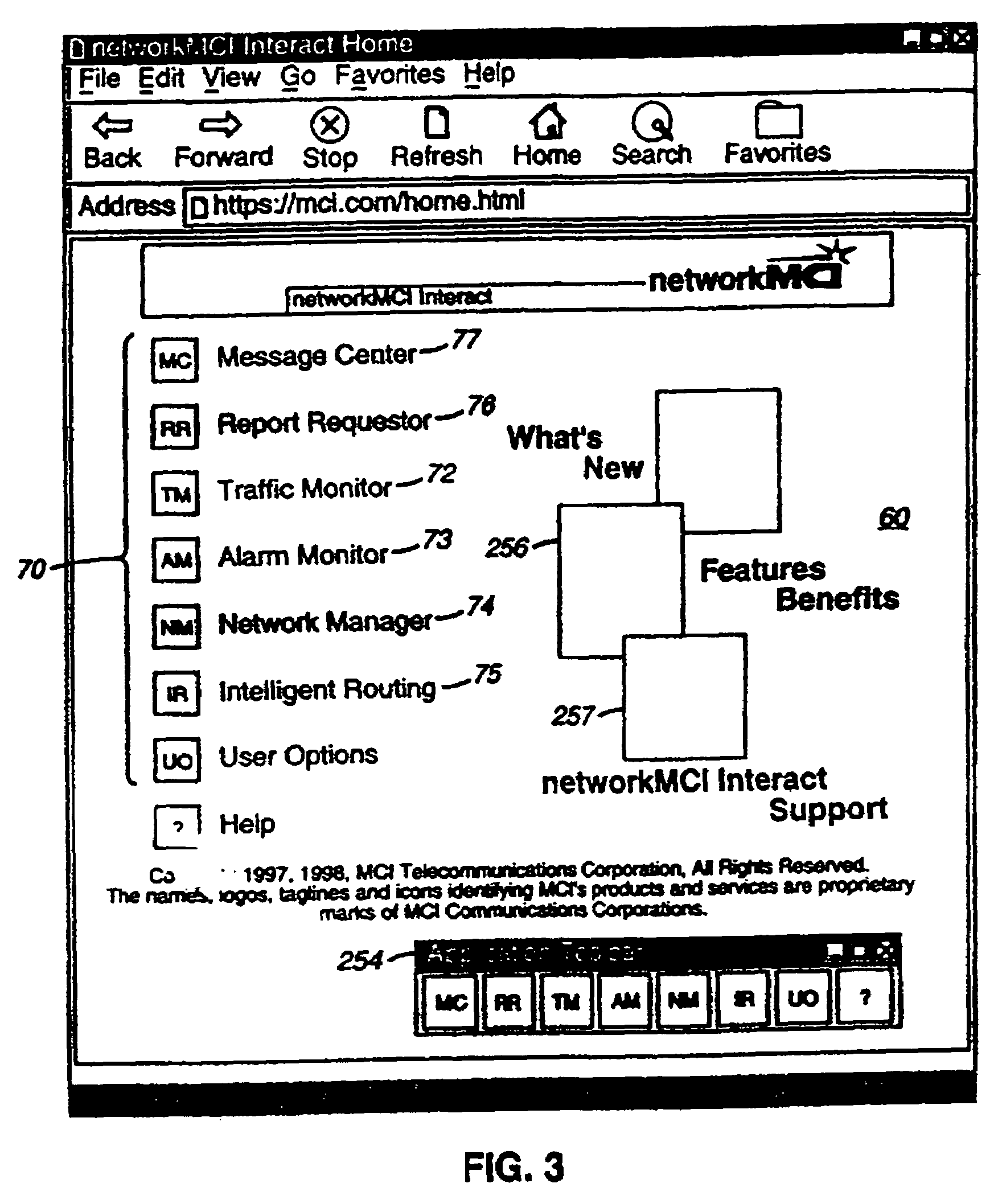
US7814533B2 - Secure customer interface for Web based data management - Google Patents
Recomendado para você
-
 Analysis Group (@analysisgroup) / X20 setembro 2024
Analysis Group (@analysisgroup) / X20 setembro 2024 -
 Analysis Group Careers and Employment20 setembro 2024
Analysis Group Careers and Employment20 setembro 2024 -
 Working at Analysis Group20 setembro 2024
Working at Analysis Group20 setembro 2024 -
 Analysis Group - Vault20 setembro 2024
Analysis Group - Vault20 setembro 2024 -
IAG, Image Analysis Group20 setembro 2024
-
 Dov Rothman - Analysis Group20 setembro 2024
Dov Rothman - Analysis Group20 setembro 2024 -
 Prigozhin interests and Russian information operations20 setembro 2024
Prigozhin interests and Russian information operations20 setembro 2024 -
 Protein Analysis Group – University of Copenhagen20 setembro 2024
Protein Analysis Group – University of Copenhagen20 setembro 2024 -
 Active North Korean campaign targeting security researchers20 setembro 2024
Active North Korean campaign targeting security researchers20 setembro 2024 -
NYU Investment Analysis Group (@stern_iag) • Instagram photos and20 setembro 2024
você pode gostar
-
 Mortal Kombat Leaked Dlc Kombat pack 120 setembro 2024
Mortal Kombat Leaked Dlc Kombat pack 120 setembro 2024 -
 Molde de vestido de boneca de pano20 setembro 2024
Molde de vestido de boneca de pano20 setembro 2024 -
 Yu-Gi-Oh! Duel Links World Championship 201920 setembro 2024
Yu-Gi-Oh! Duel Links World Championship 201920 setembro 2024 -
 85% The Witcher: Enhanced Edition on20 setembro 2024
85% The Witcher: Enhanced Edition on20 setembro 2024 -
 Como Treinar O Seu Dragão. Jogos Com Dragões Tina Gallo em Promoção na Americanas20 setembro 2024
Como Treinar O Seu Dragão. Jogos Com Dragões Tina Gallo em Promoção na Americanas20 setembro 2024 -
 Hercílio Maes: books, biography, latest update20 setembro 2024
Hercílio Maes: books, biography, latest update20 setembro 2024 -
 Jogo de lógica e observação para crianças - Tabuleiro de Dupla Entrada - Caracóis20 setembro 2024
Jogo de lógica e observação para crianças - Tabuleiro de Dupla Entrada - Caracóis20 setembro 2024 -
 My Hero Academia Season 6 Releases Jacket Cover Illustration for Ending Song SKETCH - Anime Corner20 setembro 2024
My Hero Academia Season 6 Releases Jacket Cover Illustration for Ending Song SKETCH - Anime Corner20 setembro 2024 -
 Download Charlotte Liddell album songs: Akeboshi - Kimetsu no Yaiba (2 Abertura Dublada) (Cover)20 setembro 2024
Download Charlotte Liddell album songs: Akeboshi - Kimetsu no Yaiba (2 Abertura Dublada) (Cover)20 setembro 2024 -
 Adesivos para miniaturas na escala 1/43 feito em decalque base d'água.branco ou transparente20 setembro 2024
Adesivos para miniaturas na escala 1/43 feito em decalque base d'água.branco ou transparente20 setembro 2024

